AWS IAM Policy Types
aws, iam, policy types, identity based policy, resource based policy, ACL, SCP

About
Access is managed in AWS by creating policies and attaching them to IAM identities (users, groups of users, or roles) or AWS resources.
A policy is an object in AWS that, when associated with an identity or resource, defines their permissions. AWS evaluates these policies when an IAM principal (user or role) makes a request. Permissions in the policies determine whether the request is allowed or denied. Most policies are stored in AWS as JSON documents.
AWS supports six types of policies: identity-based policies, resource-based policies, permissions boundaries, Organizations SCPs, ACLs, and session policies. This post is summary of AWS IAM policy and permission types.
AWS Policy Types
Identity-based policies
Identity-based policies – Attach managed and inline policies to IAM identities (users, groups to which users belong, or roles). Identity-based policies grant permissions to an identity.
Resource-based policies
Resource-based policies – Attach inline policies to resources. The most common examples of resource-based policies are Amazon S3 bucket policies and IAM role trust policies. Resource-based policies grant permissions to the principal that is specified in the policy. Principals can be in the same account as the resource or in other accounts.
Identity vs Resource based policy
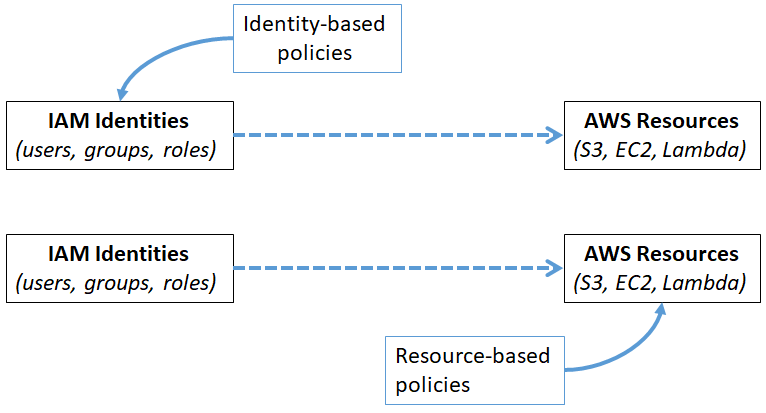 * Identity-based policies are applied to IAM identities, and grant them access to AWS resources. * Resource-based policies are applied to AWS resources, and they grant access to Principals (IAM identities, and applications)
* Identity-based policies are applied to IAM identities, and grant them access to AWS resources. * Resource-based policies are applied to AWS resources, and they grant access to Principals (IAM identities, and applications)
Permissions boundaries
Permissions boundaries – Use a customer or AWS managed policy as the permissions boundary for an IAM entity (user or role). That policy defines the maximum permissions that the identity-based policies can grant to an entity, but does not grant permissions. Permissions boundaries do not define the maximum permissions that a resource-based policy can grant to an entity.
Organizations SCPs
Organizations SCPs – Use an AWS Organizations service control policy (SCP) to define the maximum permissions for account members of an organization or organizational unit (OU). SCPs limit permissions that identity-based policies or resource-based policies grant to entities (users or roles) within the account, but do not grant permissions.
Permission boundries vs Organization SCP
- Both permission boundries and SCP only limit permissions. They don’t give any permissions.
- Permission boundries limits permissions of identity-based policies only.
- SCP limits permissions on both identity and resource based policies.
Access control lists (ACLs)
Access control lists (ACLs) – Use ACLs to control which principals in other accounts can access the resource to which the ACL is attached. ACLs are similar to resource-based policies, although they are the only policy type that does not use the JSON policy document structure. ACLs are cross-account permissions policies that grant permissions to the specified principal. ACLs cannot grant permissions to entities within the same account.
ACL vs Resource based policy
- Resource based policies can grant permission to entities in same or different account
- ACL can only grant permissions to entities in different account
- Only a few resources support ACL including AWS Amazon S3, AWS WAF, and Amazon VPC. It is a legacy IAM policy type and AWS recommends not to use it.
Session policies
Session policies – Pass advanced session policies when you use the AWS CLI or AWS API to assume a role or a federated user. Session policies limit the permissions that the role or user’s identity-based policies grant to the session. Session policies limit permissions for a created session, but do not grant permissions. For more information, see Session Policies.